03/03/2022 1,273 Alarms
Author: Victor
The Magic Systems alarm is based on a microprocessor that interacts with the key fob through a transceiver and the use of special Keeloq encoding. If security zones are violated, the anti-theft complex issues signals with a siren and car headlights. The notification is also sent to the communicator for system control (key fob, pager). For the security system to operate correctly, the voltage in the on-board network must be from 10 V to 15 V.
[Hide]
Specifications
Description of the main technical parameters of Stalker Magic Systems (MS) specified in the instructions:
- The car anti-theft system is equipped with negative outputs for connecting a siren, engine immobilizer, as well as additional channels. The latter are used to configure auxiliary equipment, for example, power windows, sunroof, side rear-view mirrors.
- The range of the pager when receiving messages is up to 800 meters, when sending commands - no more than 100 m. This indicator is conditional and depends on many factors. These include the architecture of the area, the density of buildings, weather conditions, the correct installation of the “signal”, the charge of the battery in the remote control, etc.
- The operating radius of the spare pager varies around 30 meters.
- When the protection mode is turned on, the current consumption of the security complex should be no more than 20 mA.
- The main pager is powered by batteries made according to the A23 or A27 standard, the additional one is CR2032.
- The temperature range for operation of the communicator varies from -40 to +40 degrees, the control unit - from -40 to +65 °C.
- The following zones are used to protect the vehicle: microwave controller, built-in sensitivity sensor, limit switches and ignition switch input.
- The type of impulses when security zones are violated depends on the degree of impact; it can be warning or alarming.
- The anti-theft system is protected from short circuits by means of additional safety devices.
- Data transmission between the pager and the transceiver with an antenna is carried out over a working radio channel with a frequency of 434 MHz.
Equipment
Overview of the elements included in the delivery set of car alarms Magic Systems 450 and 505:
- control device, made in a black plastic case;
- siren equipped with a speaker;
- two key fobs - one pager is equipped with a screen and a feedback function, the additional one does not have a display;
- service user manual, which allows you to install a car alarm and includes all the nuances regarding turning on, turning off and operating the system;
- sensitivity and shock sensor;
- a set of cables and connectors for connecting the system;
- limit switch for installation on the hood of a car;
- “Valet” key to enter the service mode for servicing the Magic Systems alarm system;
- electrical diagram for connecting all components;
- warranty card;
- package.
The Magic Systems alarm package does not include limit switches for installation on doors; these devices are purchased additionally.
The AvtoGSM channel presented a detailed review of the unpacking of the MC 505 system delivery kit.
Photo gallery
Photos of anti-theft systems:
Equipment MC 505
Magic Systems 450
MS 600 delivery set
Paths of Power
The Systems And Magic line of power cables consists of four models: Joker, BlackWire plus+, GoldWire and Pearl. There is no esotericism, just as there are no exorbitant prices. High-quality conductors, good connectors, neat cutting, strong shielding and... sensible division into lines. For example, low-end Joker cables definitely cannot be classified as expensive models - the only unusual thing about them is that they have a braid of different colors (this is not only a design, but also convenience during frequent reconnection). From model to model, cables evolve and their design becomes more complex. There are already expensive connectors - Wattgate for BlackWire plus+, and Pearl cables - GoldWire (plus custom plugs in aluminum outer cases with rhodium-plated connectors). In general, the cable segment (it’s worth recalling here that these are only power cables, the company does not produce signal cables) looks solid and logical, and is also clearly oriented towards combination with its own splitters and filters.
Network cables Joker (left) and BlackWire plus+ (right).
An analysis of the model range shows that the engineering approach to creating cables at Systems And Magic is as follows: a complex and multi-stage selection, including both objective measurements and subjective tests. The latter is confirmed by the fact that audiophiles from different countries describe the properties of Systems And Magic products very similarly - they note their neutral nature, they do not add their own coloring to the sound, and the products of different lines combine smoothly, virtually “seamlessly” with each other.
Older models of Systems And Magic network cables are GoldWire (left) and Pearl (right).
A few words about the “accessories” section of the Systems And Magic catalog - it contains adapters, adapters and several devices designed to check the correct connection and phasing of everything in the system. Starting from simple, but useful and understandable socket phasing indicators Pha∆ser, cable phasing device Pha∆ble and ending with a whole set of Phas∆easy, designed to check and correctly connect all components in the system, from power to various signal lines .
Key Features
List of main capabilities of MS anti-theft systems:
- Remote control of sensitivity and shock sensor. The user can independently change the settings of the sensitivity and alarm levels using a pager.
- Option “Protection against absent-mindedness”. In alarm systems from other manufacturers, this function is called “Auto-arming”. Its essence lies in the self-locking of door locks when the protection mode is accidentally turned off. If no door opens after security is deactivated, the system will re-lock them.
- Availability of “Panic” mode. With its help, the user can turn alarms on and off by command from the key fob. This will mark the vehicle as protected and scare away potential intruders from the car.
- Indication of the protection status on the communicator. The key fob display contains icons and symbols that allow you to understand whether the security is on or not.
- Bypassing non-working contact areas when turning the protective function on and off. Information about this is displayed on the device screen.
- Alarm memory. If an alarm was triggered in the absence of the user, information about this will be saved and displayed on the pager display. In addition, the manufacturing company equipped the control unit with a system status memory module. If the power supply from the control device is turned off while the security is on, then when the voltage is further connected, the system returns to its original state.
- The ability to automatically reduce the sensitivity level of the vibration sensor after the fifth operation. If the device reacts to external influences that will not affect the protection of the vehicle, the system will detect this. The controller can be triggered by cars passing by, strong wind or animals running nearby. Therefore, the control unit automatically lowers the sensitivity level to prevent false alarms.
- Application of more than 67 million combinations for transmitting and receiving packet data. The use of new codes will prevent possible interception of signals.
- Automatic start of the power unit. The essence of the function is that the user can start the engine while being at a distance from the vehicle. This will allow you to start driving in an already warmed-up car. You can configure the motor to start automatically when there are power surges in the machine's electrical network or when the ambient temperature drops to a certain level.
- Availability of a digital interface for connecting to a car. If the vehicle is equipped with a CAN bus, this will allow you to connect to the on-board network with minimal interference in its operation.
- Protection of a vehicle with the engine running. Useful feature for short stops.
A minute of Black Magic
In this article we will tell you how to learn to debug and love the little black board Black Magic Probe V2.1.
But first, a little about what it is and why it is needed. The Black Magic Probe Mini V2.1 (BMPM2) board, developed by 1BitSquared in collaboration with Black Sphere Technologies, is a JTAG and SWD adapter designed for programming and debugging ARM Cortex-M and ARM Cortex-A microcontrollers. You can add support for other processors. A description of the adding process can be found here. It's also worth noting that any processor that supports ADIv5 (ARM Debug Interface v5) will be detected by the board.
The figures show ARM Cortex-M and ARM Cortex-A family processors supported by the Black Magic Probe Mini V2.1 board.
During testing of the Black Magic Probe, it was revealed that the supported processors are not limited to the list provided by the manufacturer. Officially unsupported processors with ARM Debug Interface v5 are defined, for example, as “Cortex-M0” or “Cortex-A7”. At the same time, full functionality is not guaranteed, but it will still be possible to perform minimal debugging steps.
What you can do with the Black Magic Probe board:
- interrupt the program execution process;
- monitor changes in registers and variables;
- set breakpoints (you can set a breakpoint in your code that will cause the program to stop as soon as that point is reached);
- view the call stack (a list of functions and their parameters that led us to the current point and state of the program);
- disassembly (the ability to view machine code and find out what exactly the program does);
- memory dump (saving RAM and/or flash content to a file).
Black Magic Probe features that may be useful when researching device information security:
- development of embedded software and devices for carrying out attacks;
- IoT reverse engineering;
- searching for vulnerabilities;
- dynamic analysis using IDA and other tools compatible with gdb servers.
BMPM2 has two main features. The first is that the device itself runs a gdbserver, which opens a virtual port that you can directly connect to via the gdb client on your host machine (the gcc-arm-embedded toolchain is recommended), so there is no need to configure OpenOCD or STLink configurations. A comparison of the debug interface connection diagrams using OpenOCD/STLink and BMPM2 can be seen below. As you can see, the option with connecting via BMPM2 is simpler.
The second is the ability to compile the firmware for other boards, eliminating the need for BMPM2. Compatible boards are presented here.
To study the possibilities of operation, four boards were taken: TM32F103C8, STM32vldiscovery, STM32F429I-disc1 and 1Bitsy V1.0 offered by the developers.
Working with 1Bitsy and STM32F429I-disc1 will be discussed in more detail. The first was chosen on the recommendation of the developers themselves, and the second has a touch screen, which makes the research process more visual.
Let's explore the world of debugging with Black Magic Probe
It’s convenient to start learning how Black Magic Probe V2.1 works by debugging 1Bitsy. This board was designed specifically to work with BMPM2, so there shouldn't be any problems. Let's connect Black Magic Probe and 1Bitsy to each other with a JTAG cable and connect them to the computer. Below we will describe working in the GNU/Linux environment; instructions for working in Windows and MacOS can be easily found by following the link.
After connecting BMPM2 to the PC and to the JTAG connector, on 1Bitsy we will execute three commands in gdb to begin debugging. It is important that the user is added to the dialout group with the command “sudo adduser $USER dialout”, otherwise nothing will work. The first command “target extended-remote /dev/ttyACMx” connects to BMPM2, where x is the serial port number, then we scan all devices connected to the Black Magic Probe using the “monitor jtag_scan” command. If all is well, a list of found devices will be displayed and with the “attach 1” command we will connect to 1Bitsy.
(gdb) target extended-remote /dev/ttyACM0 Remote debugging using /dev/ttyACM0 (gdb) monitor jtag_scan Target voltage: 3.3V Available Targets: No. Att Driver 1 STM32F4xx (gdb) attach 1 Attaching to Remote target warning: No executable has been specified and target does not support determining executable automatically. Try using the "file" command. 0x0800026c in ?? () (gdb)
That's it, now we can debug the firmware uploaded to 1Bitsy. With 1Bitsy, there really weren’t any connection problems; everything was simple and quite convenient. Will the simplicity and convenience remain the same when working with another board?
We had a board based on the STM32 microcontroller - STM32F429I-disc1, we will use it, and at the same time we will upload some interesting firmware to it. The main difference between working with this board and working with 1Bitsy is the connection via the SWD interface, rather than JTAG.
Before starting work, we connect the boards via a JTAG/SWD adapter according to the following scheme: on the SWD interface (if counted from the topmost output):
- SWCLK
- GND
- SWDIO
- 3V - tVref.
To demonstrate the functionality of the debugging process, firmware containing several software modules was used. One of them is the game Reversi, which will be the most interesting to debug.
We upload the firmware to the board and enter almost the same commands into gdb as for 1Bitsy, with the only difference being that the board is connected via SWD, so you will need to use the swdp_scan command.
(gdb) target extended-remote /dev/ttyACM0 Remote debugging using /dev/ttyACM0 (gdb) monitor swdp_scan Target voltage: 3.3V Available Targets: No. Att Driver 1 STM32F4xx (gdb) attach 1 Attaching to Remote target warning: No executable has been specified and target does not support determining executable automatically. Try using the "file" command. 0x0800026c in ?? () (gdb)
Unfortunately, we never managed to win, so we wanted to break something in it. To begin with, we looked at the sources. The Board variable was found in them, presumably indicating the address of the first cell of the board. Nearby there are the lines “Reversi - Player 1” and “Reversi - Player 2”.
static void _SetPlayer(int Player) { int Score, ValidMoves, PossibleMoves; char ac[256]; _Board.ActPlayer = Player; if (Player == 1) { FRAMEWIN_SetText(_hFrame, "Reversi - Player 1"); } else { FRAMEWIN_SetText(_hFrame, "Reversi - Player 2"); } FRAMEWIN_SetBarColor(_hFrame, 1, (Player == 1) ? GUI_RED : GUI_BLUE); PossibleMoves = _CalcValidMoves(&_Board); GUI_Exec(); if (!PossibleMoves) { GUI_Exec(); _Board.ActPlayer = 3 - Player;
We searched these lines in the IDA disassembler. We found out that from the pseudocode you can find out the address, which is the starting address of the board cells.
v1 = a1; v2002CB74 = a1; if ( a1 == 1 ) { sub_D8B3C(v2002CB80, "Reversi - Player 1"); v2 = 255; } else { sub_D8B3C(v2002CB80, "Reversi - Player 2"); v2 = 16711680; } sub_E06A8(v2002CB80, 1, v2); v3 = sub_DEDF8(0x2002CAF4); result = ((int (*)(void))sub_C91B4)(); if (v3) return result; sub_C91B4(result); v2002CB74 = 3 - v1; v5 = sub_DEDF8(0x2002CAF4);
Next, we decided to use gdb to see what was located at this address.
That's right. If you carefully study this table and the location of the chips at the beginning of the game, you will notice that 001 means a red chip, and 002 means a blue one. You can try changing the value of one of the cells. To do this we used the command:
set *(char *) 0x2002CAF4 = 1
Result:
After that, we decided to try to equate the values of all cells to one, and thereby win the game on the first move.
Result of script execution:
The script worked successfully, we managed to win the game, which means that using the Black Magic Probe Mini V2.1 board via gdb we can successfully debug and “break” the firmware. And now some boring examples with blinking lights.
STM32F103C8
We will connect the STM32F103C8 board to Black Magic Probe V2.1 via the JTAG interface.
The source code for flashing the board can be found here.
In the source code, you can try to change the speed at which the light bulb blinks, decreasing or increasing the time intervals when it is on and when it goes off.
STM32vldiscovery
Let's connect the STM32vldiscovery board to Black Magic Probe V2.1 via the SWD interface, namely:
- 3V3 - tVref
- PA13 - SWDIO
- PA14 - SWCLK
- GND - GND
The source code for flashing the board can be found here.
Here everything is similar to the previous board, we also change the time intervals in the source code and look at the light bulb.
conclusions
The Black Magic Probe Mini V2.1 board is easy to use and has a set of open source tools and libraries, these are its main advantages. The disadvantage of the board is the lack of support for the architecture of arm64 processors and Texas Instruments processors.
https://1bitsy.org/overview/introduction/ https://1bitsquared.com/products/black-magic-probe https://github.com/esden/1bitsy-bmpm-exercises/blob/master/embedded_programming_with_black_magic_and_lights_on-workshop_guide .pdf https://github.com/blacksphere/blackmagic/wiki
Authors
- Evgeniy Rasskazov Jokiv
- Valeria Gubareva veneramuholovka
Advantages and disadvantages
Overview of the main advantages:
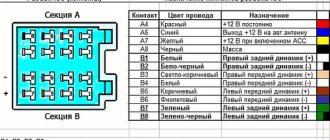
- Availability of a detailed Russian-language service manual for managing and configuring the system. The manufacturing company indicated in the documentation not only the electrical diagram, but also recommendations regarding the connection of certain contacts on the connectors.
- Possibility of additional connection of a GSM module, with which the user can determine the coordinates of the vehicle. The device can be controlled using commands sent from the phone or using a mobile application for a smartphone.
- According to the manufacturer, all Stalker Magic Systems systems are equipped with 100% protection against electronic hacking and signal interception. For this purpose, the author's encryption technology is used.
- Availability of 24/7 technical support. If questions arise, the user can contact company representatives at any time to clarify issues regarding the operation of the alarm.
- Silent operation of the security system thanks to the use of a solid-state power unit blocking relay. In the event of a break-in, criminals often calculate the location of the “signaling” control unit based on the sound (clicks). This is not possible with Magic Systems.
After analyzing consumer reviews, the following disadvantages can be identified:
- Rapid wear of the communicator. With prolonged and intensive use, the pager body becomes worn, and the buttons may become stuck.
- The key fob functions intermittently. To send commands to the control unit, the user has to press the keys several times.
Systems and Magic Black Noise 1000 review. Magazine "Audio Store"
Black Noise 1000 refines the sound, giving it richness, velvety and plasticity. Flexible nuances and a hall effect reminiscent of reverberation without the boominess evoke a sense of the performers' presence in front of the listeners.
Save and read later -
Systems and Magic Black Noise 1000 surge protector
External (and internal) view
Compact but heavy box with two sockets made by Vimar (Italy) on the top panel. It is almost impossible to disassemble the filter; you can only see that the lion's share of the internal living space is occupied by a compartment filled with blue compound. The body rests on small, hard, rounded rubber feet. Network cable not included.
Ideology and design according to the manufacturer
Four stages of filtering are used in the neutral and “hot” wires, plus two-stage filtering in the “zero” (“ground”) wire. The filtering is bidirectional, that is, it not only protects against interference coming from the electrical network, but also suppresses the further spread of interference that occurs inside the components connected to the filter. There is protection against pulses and voltage surges above 250 V. The fuse is implemented as a thermal breaker, which does not limit the current consumption of the amplifiers, but protects against overload caused by exceeding the rated power consumption. The blue LED lights up when the thermal protection is triggered.
The circuit uses about 30 high-quality radio components: polypropylene capacitors, powerful resistors, chokes. They are mounted on a main board made of 2 mm fiberglass with powerful printed conductors 70 microns thick, equivalent to a single-core copper wire with a cross-section of 2.5 mm2. For mechanical stability and vibration damping, the board is filled with a special epoxy compound. The 4mm thick extruded aluminum body features a monocoque design and is precision CNC machined.
Country of origin: Italy.
Sound quality
This compact device differs significantly in sound character from the usual air conditioners of the “old stock”. Black Noise 1000 refines the sound, giving it richness, velvety and plasticity. Flexible nuances and a hall effect reminiscent of reverberation without the boominess evoke a sense of the performers' presence in front of the listeners. It seems that the air conditioner itself is an active inductor of a surround sound stage, reminiscent of the real acoustics of a concert studio. The lower register - articulated, clear - contributes to the free and expressive sound of large orchestras. Digital recordings acquire the desired spirituality. Fine detail throughout the entire dynamic range and stable tonal balance across a wide frequency range are confidently maintained.
Thanks to the filigree of the middle and upper registers, as well as the deep, well-articulated bass, the musical text is easily and accurately perceived by a musically literate listener, which encourages him to admire the music more, consciously observing its movement, the development of musical events, rather than subconsciously enjoying it. Soft velvety, once familiar, caressing the ear and plunging into a meditative state, is gradually leaving the audio world, but its successful combination with the piercing clarity and crystal purity of sound inherent in the Black Noise 1000 tract can completely enchant the listener with musical surprises on well-known soundtracks .
Black Noise 1000 corresponds to its price category and meets the requirements of modern “high fashion” in terms of musical expressiveness and sound comfort. It can interface with any reasonably designed audio paths. Considering its affordable price, Black Noise 1000 can be recommended to a wide range of listeners with different musical tastes and sound preferences.
Prepared based on materials from the AudioMagazine magazine, September 2009
www.audiomagazine.ru This review was read 9,145 times
Installation instructions
Before installing Magic Systems, it is recommended to connect the system components to the battery separately, without installing it on the car, to ensure that the alarm system is working properly.
Installation Guide:
- The car's battery is disconnected. It is located under the hood; you need to disconnect the terminal clamp with the negative contact from the device.
- The microprocessor unit is located in the car interior, away from sources of high temperatures, moisture and moving parts. The module is equipped with a built-in sensitivity controller, so the user must ensure a high-quality and reliable connection of the device to the surface. Plastic clamps or glue are used for fixation.
- The transceiver with antenna is installed on the inside of the windshield, which should not be equipped with a built-in heater. It is recommended to position the module in the center and secure it using double-sided tape. There should be no metal body parts near the device, as well as electronic equipment - car radio, on-board computer. When laying cables, it is recommended to move the electrical circuits 10 cm away from the module, coaxially with the antenna.
- The siren should be placed under the hood of the car in the place that is most protected from access from under the bottom. Do not install the speaker near heating components, the cylinder head or other metal surfaces adjacent to it. Its socket should be installed downward so that moisture does not collect in it. The connections must be made inside the car to prevent oxidation of the contacts on the wires. The cables are routed from the engine compartment into the car through a special hole in the partition.
- Limit switches are installed on the hood, trunk and all car doors. When they are locked, the stroke of the device rod should be at least 6 mm. After installation, you need to make sure that there is no access to the “limit switches” from the outside when the doors are locked.
- The LED light bulb is located in the vehicle interior. It must be placed so that the operation of the diode can be seen from the street. The device must be installed so as not to disturb the interior of the cabin.
- The key to enter the service mode should be located in the car interior as discreetly as possible. Installation can be carried out in one of the bundles with standard wiring under the dashboard of the car. This will allow you to “disguise” the button by wrapping it with electrical tape, as well as provide full access to it from the driver’s seat. And this is mandatory, since the key can be used to disable the security system in an emergency.
Auto electrician Sergei Zaitsev spoke about the features of installing anti-theft systems on vehicles and their connection using the example of Daewoo Lanos.
Quadruple, six and eight
The next large group of Systems And Magic products are network splitters. They partially function as filters (the design includes protection against power surges), but otherwise they are classic and well-made “audiophile” distributors that will appeal to connoisseurs of a purist approach to system power. And also for those who do not have obvious “network” problems in the house and who own components that do not really get along with filters (and such components do occur). However, the manufacturer allows the use of both BlackNoise line filters and network splitters in one system - moreover, this approach is logical and justified.
Network splitters Systems And Magic Duplex (left) and Derive (right).
And in this vein, it’s worth studying the younger model - Duplex. In fact, this is the most common adapter, with one plug-in and two sockets at the output. Only the entire structure was made according to audiophile criteria. It can be supplemented with any of the filters in the BlackNoise line, adding one socket in cases where it is needed, but in terms of power and other criteria, one filter is enough.
The device will also be useful for those who, for a number of reasons, cannot lay dedicated lines to the system and install expensive network components - for example, in a rented apartment, when there is only a regular outlet near the rack. Or when you need to power only a couple of high-end components, but something complex in terms of power supply is not available. To some, such things may seem unnecessary, but nevertheless it is an interesting option that will help improve the system in difficult situations.
The remaining network splitters have a more familiar design, and their model range is tailored to almost all audiophile tasks. Some of the most famous and widespread Systems And Magic models are Four, Six and Eight splitters. The names of the devices are self-explanatory - they are equipped with four, six or eight input sockets. The splitters are assembled in massive aluminum housings, already familiar to us from the line of filters, with additional damping; they contain expensive components, Vimar sockets.
Systems And Magic Slim3 (left) and Six (right) splitters.
In turn, the design of the Derive splitter is a little simpler, and the body is smaller. But there is a standard half-meter network cable installed (the company offers two modifications with wires from different Systems And Magic lines). The device is self-sufficient, but the developers recommend pairing it with BlackNoise to get eight sockets from one filter and two Derive splitters, which is enough to power most systems.
Finally, the line of splitters is completed by two simple models: Slim3 and Slim5 (three and five sockets, respectively). They are assembled in narrow cases, and the sockets are arranged in one row. By the standards of Systems And Magic, these are basic models, but in comparison with many other manufacturers, they are very high-level designs.
User manual
After installation, it is recommended to ensure that the alarm is connected correctly. To do this, you need to enable and disable auto protection mode. If the system closes and opens the doors, then the elements are connected successfully.
Control key fob
Before using the remote control, you need to install a working battery in the device. The power supply is inserted into a special compartment located behind the rear protective cover.
Designation of symbols on the key fob
Indication on the display of the main pager using the example of the MC 600 Stalker model:
Description of icons on the Magic Systems screen
Symbols:
- Vehicle protection mode is enabled.
- Activation of the service mode for system maintenance and open access to the programming menu.
- Reduced sensitivity of the built-in controller.
- Alarm indicator.
- Autostart alarm is enabled or disabled.
- Car perimeter security using a microwave sensor.
- Internal vehicle protection through additional controllers.
- Reservation of the automatic engine start function.
- Board with the current time. This field can contain information about the alarm being triggered.
- Battery charge indicator in the key fob.
- Disable key fob confirmation beeps, only vibration works.
- Two-way communication with the vehicle.
- Signal from a tripped limit switch located in the trunk door.
- Open car door.
- A running car power unit.
- A symbol that allows the implementation of the engine autostart function.
- Indication of entry into the settings and programming menu.
- Security mode disable icon.
- The “Mushroom picker” option is activated. When it is launched, the alarm mode will be accompanied only by visual optical signals. This will allow you to find a car left in a large parking lot.
- Beach mode is on. When using it, the security will be activated with a time delay.
Identification of buttons and alarm signals
Indication of icons and keys on the Magic Systems 600 alarm panel:
Identification of buttons and alarms
Description of elements:
- Duration of pulses when alarm mode is activated.
- Notifying the car owner when alarms are triggered.
- The siren turns on as a result of the external zone of the shock sensor being triggered.
- Recording strong physical impact on the body.
- Alerts the car owner about a weak impact on the car body.
- The car's ignition is turned on.
- Vehicle security.
- Buttons for alarm control. Key with a closed lock - 1, with an open lock - 2. When an alarm is triggered, these elements allow you to turn off the siren.
- Internal microwave sensor area.
- Car tilt control icon.
- Determination of door lock zones.
- The siren signal was triggered by impulses from the limit switches of the luggage compartment or hood.
- Button C is number 3. Used to deactivate the alarm.
- Audio messages are disabled.
Key fob programming
To add information about new remote controls to the memory of the microprocessor module, perform the following steps:
- When the ignition is turned off and the security mode is turned off, a code for service is entered. Initially, Magic Systems alarms are assigned a password of 123.
- You need to press key 1 once, then control 2 is “clicked” twice. Button 3 is pressed three times. If a different code is used, then the number of clicks must correspond to the digits of the password.
- The function programming menu is entered.
- Button 1 is pressed and must be held in this position for 2 s. After the “click”, the diode light bulb will fire with an extended flash. This indicates that information about the key fob has been entered into the microprocessor memory. Similar actions are performed with each registered communicator.
Setting up autorun
To configure the parameters for automatic engine start with Magic System alarm, the user must prepare the car for the implementation of this function:
- If the anti-theft system is equipped with a special button for remote engine start, you must press it. The power unit must be started.
- On a car with a manual transmission, the lever is moved to the neutral position. On automatic transmissions, the selector is set to “Parking” mode.
- The user raises the handbrake. If, when activated, the car may roll, then it is also necessary to install wheel chocks under the wheels. You can use a regular brick or a special “shoe”.
- Then the ignition should be turned off. The key is turned to the “Off” position and removed from the lock. On vehicles with an automatic transmission, the engine will stop at this moment; on vehicles with a manual transmission, it will continue to run. A message about autorun preparation will be sent to your communicator.
- Over the next 60 seconds, the user leaves the car and closes all doors. The security mode is activated. In a car with a manual transmission, the engine must stop.
Features of setting the function:
- You enter the anti-theft system programming menu. To do this, you need to press the first button on the remote control. Depending on the model, the steps may vary.
- Using the up and down arrow keys, select the required command. The cursor on the key fob display must be set to the position of the icon labeled “Start”. To confirm the function, press the same button used to enter the menu.
- When the engine starts successfully, the key fob will play a triple beep. If the start-up is not carried out, the number of pulses will be 4 pcs. To disable autorun, the cursor must also be moved to the position of the indicator labeled “Start” and the option must be deactivated.
Programmable operating modes
The principle of setting functions using the programming method:
- The password is entered using the service button.
- You enter the menu for changing parameters using the key fob. All functions are listed in the table and have a specific number. For example, if you need to set the sensitivity of the shock sensor to maximum, then this is the value of options 2.3.8. The user must first double-click one of the key fob buttons (any). Then three times on another key, and 8 times on the third control.
Options programming table:
| Function in menu | Meaning |
| 1. Reset all alarm settings to factory settings | 1.5 - settings deactivation menu |
| 2.1 Automatic engine start | Peculiarities:
|
| 2.2 Remote engine start by command from the key fob | If the value is 2.2.1 the function is disabled, if 2.2.2 the option is activated |
| 2.3 Adjusting the sensitivity parameter of the built-in sensor | In values from 2.3.1 to 2.3.8 the consumer selects the required level. In position 2.3.1 the controller is disabled. |
| 2.4 Automatic return of the vehicle to protection | 2.4.1 - function disabled, 2.4.2 - enabled |
| 2.5 Automatic arming of the car | Option values:
|
| 2.6 Intelligent car security | In position 2.6.1 the function is disabled, in 2.6.2 it is enabled |
| 3.1 Commands to activate protective mode | Description:
|
| 4.1 Intelligent protection mode | Peculiarities:
|
| 5.1 Method of blocking the power unit | Description:
|
Alarm Identification
Description of alarm impulses:
- One short siren signal and 1 optical flash indicate that the outer zone of the built-in shock sensor is turned on. In this case, information about a specific area is displayed on the pager display. The key fob will play two pulses - one melodic and one short.
- If the physical impact on the vehicle body is weak, then the number of warning signals will be from one to seven. Their number depends on the degree of impact on the body. The pager will play a double beep.
- A strong blow to the body is accompanied by activation of the siren for 30 seconds, during which time the parking lights will flash. The corresponding icon will be displayed on the key fob screen, and the device will play a triple signal. The Magic Systems system reproduces similar impulses when the internal zone of the sensor is triggered.
- When the door lock protection or ignition system is activated, the duration of the siren will be 30 seconds. But the pager speaker will work with one melodic and five short signals.
- If the tilt controller turns on, alarm signals are played for thirty seconds, and the car's lights work for the same amount of time. An icon in the form of car wheels will appear on the communicator screen.
How to turn off the alarm
The user has two options for deactivating the anti-theft system - using a communicator and a personal password.
Basic shutdown
Turning off the security mode using the key fob:
- The user must enter the operating range of the transceiver. You must approach the vehicle.
- Briefly press the up arrow button. The communicator's controls will be unlocked and the display backlight will turn on. Then the down arrow key is clicked three times. The characters on the screen will begin to blink.
- A command is selected to disable the function using the cursor method. The action is confirmed, after which the pager will send the required option to the control unit via the transceiver. The remote control will play one short beep.
- The car doors will open and the lighting devices will blink twice. The corresponding icon will appear on the pager screen.
Service shutdown
To service deactivate the security, the following actions are performed:
- The ignition in the car is turned off; to do this, the key must be turned to the “Off” position.
- Over the next 10 seconds, the user must enter password 444. This will allow you to enter the service deactivation menu.
- Within 10 s, the personal code is entered.
Download installation and operating instructions for the Medzhik alarm system in pdf format
You can download service manuals for installation and use using the following links:
| Manuals in Russian for operation and installation of alarm systems | |
| Magic Systems 450 Operating Instructions | |
| Installation instructions for Magic Systems 450 | |
| Operating instructions for Magic Systems 505 | |
| Installation instructions for Magic Systems 505 |
Video
The “BREACH CAR” channel in its video presented the results of a test of the range of the MC 600 Stalker car anti-theft system.
Do you have any questions? Specialists and readers of the AUTODVIG website will help you ask a question
Was this article helpful?
Thank you for your opinion!
The article was useful. Please share the information with your friends.
Yes (100.00%)
No
X
Please write what is wrong and leave recommendations on the article
Cancel reply
Rate this article: ( 1 vote(s), average: 5.00 out of 5)
Discuss the article: